
Secure and Efficient Application Modernization with Calico
February 6, 2024
Address and simplify this challenge with the most widely used container networking and security solution.
In today's context, where agility and growth are essential, microservices architectures have become a predominant trend within the field of software development.
However, transitioning from a monolithic and less scalable structure to one divided into smaller and more scalable blocks, while offering multiple benefits, also entails significant challenges in terms of security.
This is because traditional solutions in this field are not equipped for such architectures due to their lack of granularity, limited scalability, lack of observability, management complexity, and excessive time consumption.
These challenges underscore the importance of addressing security in microservices architectures early on, using specialized strategies and tools to protect, strengthen, and continuously monitor them.
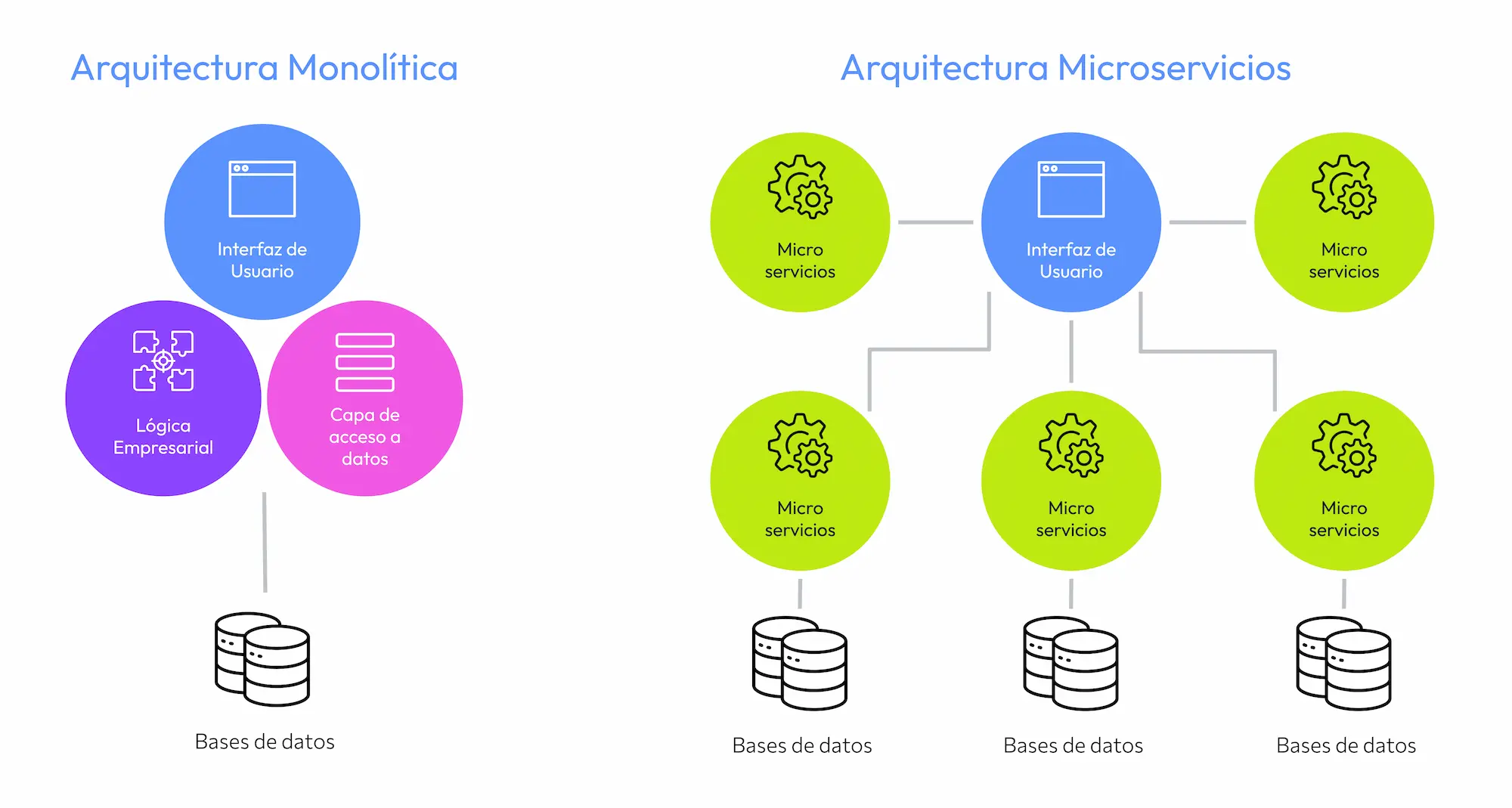
Classic Monolithic Applications vs Microservices
Monolithic applications are characterized by their single, centralized structure, where all functions converge into a single block of code. In contrast, microservices represent a distributed architecture, decomposing each function into independent services that collaborate to achieve the final goal.
From a scalability perspective , microservices offer superior flexibility. Each service can scale independently according to demand, unlike monolithic applications, which often require duplicating the entire infrastructure to scale capacity.
However, monolithic applications often have maintenance advantages by concentrating everything in one place. In contrast, , managing microservices can be more complex, requiring coordination between independent services.
Additionally, microservices stand out for their efficiency. Their ability to scale individually and their intrinsic modularity make thema more efficient option, especially when seeking to optimize resources and adapt to changes in demand rapidly.
Containers as Basic Blocks
When exploring the universe of microservices, the term “container” emerges as a central and essential concept, as they offer exceptional flexibility and portability in the deployment of applications.
The ability to encapsulate all the elements required to run an application, from code to libraries and dependencies, gives containers the ability to move effortlessly between development, testing , and production environments. Their efficiency is highlighted by sharing the same underlying operating system, outperforming traditional virtual machines.
In this context, Docker stands as a cornerstone in the implementation of microservices, although it is essential to note that, in certain scenarios, this product could be limited when implementing cluster-based applications.
Kubernetes for Service Scaling
Kubernetes, the quintessential container orchestrator, has become an essential tool for managing and scaling of microservices today, almost considered an industry standard.
With Kubernetes, development teams can simplify the management of containers and server clusters, allowing them to focus on building innovative applications.
One of the outstanding advantages of Kubernetes is its automatic ability to scale services based on demand. If a service experiences a sudden spike in traffic, Kubernetes can automatically increase the number of replicas for the service to meet the demand.
This approach ensures that applications are highly available and scalable, giving development teams the necessary confidence in the performance of their applications.

Challenges in using Kubernetes
Implementing systems with Kubernetes brings with it a number of challenges that span security, observability, management, compliance, and reporting.
Security
One of the main challenges that companies face when adopting microservices is security. Fragmenting an application into multiple services creates a broader and more complex attack surface, increasing the risk of vulnerabilities and security breaches. Applying security measures, such as authentication and authorization, is essential to protect critical data and systems.
For example, suppose we have a financial application that processes transactions. We need to establish security policies to ensure that only authorized containers access critical data, avoiding lateral movement between different pods.
Observability
Another challenge is observability, which involves monitoring and diagnosing the performance and behavior of microservices. With interconnected services, identifying and resolving performance issues or errors in business logic can be complicated. Proper monitoring and logging tools are essential to ensure service availability and quality.
Continuing with the financial application, we need to provide detailed information about network traffic to quickly identify performance problems. Without the right tools, detecting application bottlenecks is difficult and essential for site reliability engineers.
Other Challenges
In addition to those mentioned above, we also face challenges in management, compliance and reporting. This is where the Calico tool comes in as a possible solution, offering help in these aspects.
Calico, the Open Source Project
Calico is an open-source project dedicated to providing networking and security solutions for microservices environments , using the CNI (Container Network Interface) standard . This project stands out for several key characteristics that position it as an essential tool for network management in complex environments.
Key Features
Calico distinguishes itself by being highly useful in the management of networks in complex environments, offering exceptional flexibility and scalability in the deployment of applications. Its seamless integration with Kubernetes and other orchestrators makes it easy to deploy in diverse environments.
Additionally, Calico offers advanced security solutions, such as tag-based network policies and container isolation. These features ensure effective protection of sensitive application data and thus the enterprise, providing a secure and reliable environment.
But who is behind Calico?
Tigera, the Company
Tigera is a company specialized in providing Calico-based enterprise solutions, with a focus on two outstanding offerings: Calico Cloud and Calico Enterprise.
About Calico Cloud and Calico Enterprise
Tigera, through Calico Cloud and Calico Enterprise, is dedicated to helping businesses deploy microservices securely and efficiently, allowing them to take full advantage of the benefits of this innovative architecture.
Calico Cloud is presented as a comprehensive cloud security and network management platform. This solution facilitates the deployment of microservices by offering key features such as network provisioning automation, network traffic monitoring, and cyber threat protection.
In contrast, Calico Enterprise is an advanced security solution that provides additional features, including network segmentation and intrusion prevention. Both solutions, based on Calico opensource, guarantee optimal performance backed by the product's extensive experience in the field.
Integrating these solutions into the business environment gives organizations the confidence to deploy and manage their microservices effectively and securely.
What can I do with Calico?
With Calico Cloud or Enterprise, securing and managing microservices becomes efficient, offering a wide variety of tools for security, compliance, management, and application observability.
These solutions allow you to configure advanced security policies, monitor network traffic in real time, generate detailed reports on application performance, and much more. Seamless integration with Kubernetes and other orchestrators makes it easy to scale services quickly and easily.
Common Use Case Examples
Imagine a healthcare application that stores patient records. With Calico, it is possible to enforce security policies so that only authorized pods access confidential patient information, avoiding lateral movements between different pods.
In an environment with a health application that requires protection, Calico can be used to encrypt inbound and outbound communications between pods. This ensures protection against possible leaks of data flows, guaranteeing the integrity and security of information in transit.
Benefits of Using Calico Cloud/Enterprise
Calico Cloud/Enterprise emerges as a comprehensive solution for the secure and efficient deployment of microservices in enterprise environments, providing several significant advantages.
Security and Privacy
Confront external threats and safeguard the privacy of your customers' data by providing a reliable and robust layer of defense.
Improved Management
Transforms the complexity of managing networks and security in multi-cloud and multi-orchestrator environments into a simple task. This frees businesses to focus on their core, without worrying about the underlying infrastructure.
Strong Points Regarding Opensource
Explore a graphical interface that facilitates management, promoting a quick and enjoyable learning curve.
Calico Cloud Advantages
Discover an ally in management, the Web Application Firewall (WAF) and a specialized approach to container security.
Perform accurate pre-deployment inspections, detect unusual pod behavior , and achieve rapid deployments in minutes. In addition, it has extensive support for the most common distros, such as AKS and EKS.
Benefits of Calico Enterprise
Immerse yourself in a deep security and observability experience , with the ability to choose data plans based on your needs. Experience an integrated WAF, detailed packet inspection, and extensive support for various distros and cloud environments.
Conclusions
In summary , adopting microservices provides superior scalability, flexibility, and efficiency compared to traditional monolithic applications. However, it faces notable challenges in security, management and regulatory compliance.
To address these challenges, tools like Kubernetes, containers, and projects like Calico emerge as valuable resources. Likewise, enterprise solutions like Calico Cloud and Calico Enterprise stand out by offering a secure and efficient approach to deploying microservices in the enterprise environment.
Enhance Connectivity and Security in Distributed Architectures
SNGULAR and Tigera have entered into a strategic collaboration to address connectivity and security for microservices and Kubernetes challenges in next-generation distributed application architectures This partnership seeks to simplify the lives of DevOps professionals and mark a milestone in the technological world.
At SNGULAR, we are not only your technology provider, but a trusted partner committed to helping you meet and exceed your ever-evolving expectations.
If you are interested in improving your company's performance , we can help you develop unique solutions to meet your specific business needs. We work with you hand in hand, strategically using technology to optimize your processes and take your company to the next level.
Our latest news
Interested in learning more about how we are constantly adapting to the new digital frontier?

Tech Insight
April 2, 2025
🧐 What is Mockoon and why should you use it?

Corporate news
March 21, 2025
We are already Atlassian's partner in the United States

Insight
February 18, 2025
The Transformative Power of AI in Health and Pharma

Insight
January 23, 2025
Scrum roles and responsibilities: a step towards transparency and engagement
